
AWS vs Azure - Object Storage - Valet Key Pattern Part 1
So far in this series, we’ve covered a lot of the technical aspects of object storage and have explored how they are implemented in both cloud providers. For this post, I’d like to examine a cloud architecture pattern called the valet key pattern, and discuss how to implement this in both Azure and AWS. In this post, lets talk about what the valet key pattern is.
Please note that most of this content is based off of the cloud architecture patterns book. https://docs.microsoft.com/en-us/azure/architecture/patterns/valet-key
Traditionally, web applications have always acted as a gateway for user access to protected resources. This becomes quite apparent when you think about databases that back these applications. They are a protected resource, and the web application provides limited access for users to interact with those database resources.
Databases are not the only resources that web applications can act as a gateway for. For many applications, other services such as storage could be in use. Think about an application that ingests video for downstream processing/hosting. Other examples could be APIs that place transactions to back-end systems.
On-premises systems architecture would general hide these types of protected resources from external access. This is obviously a security best practice, especially when the same “storage” engine is being used for all types of data. In the cloud, however, it is possible to create resources for only a specific purpose. Further to this, cloud resources such as storage and queues are already available on the internet by default. The protection mechanism of those resources have shifted from network controls to user based controls.
Because of this, both internal facing and external facing web applications can make use of the valet key pattern. The pattern looks something like this:
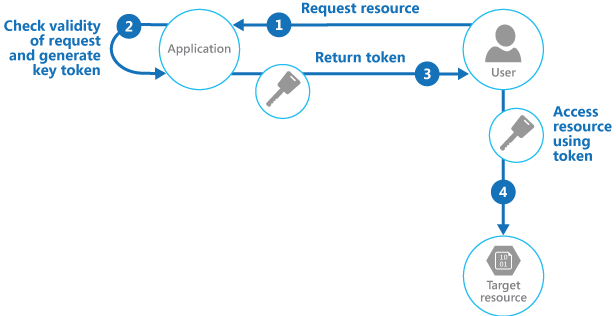
Effectively, instead of the web application proxying access to protected resources, it acts as a gatekeeper for credentials/access decision only. Let’s take the example of a user wanting to upload an image for processing purposes.
- User requests access to upload a file for processing
- Application checks the request (authentication and authorization)
- Application provides a temporary access token that grants the user appropriate permissions to perform the requested action
- User interacts with the protected service to perform the desired action
There are obviously pros and cons to the above approach, which I won’t dive in to here. Most of them are trying to strike a balance between usability of the solution and bandwidth/performance considerations.
In terms of object storage, this pattern is applicable in both AWS and Azure. For AWS, we will be using the secure token service to provide a temporary token and we will take a look at signed URLs. For Azure, we will simply provision a shared access signature with the required permissions.
About Shamir Charania

Shamir Charania, a seasoned cloud expert, possesses in-depth expertise in Amazon Web Services (AWS) and Microsoft Azure, complemented by his six-year tenure as a Microsoft MVP in Azure. At Keep Secure, Shamir provides strategic cloud guidance, with senior architecture-level decision-making to having the technical chops to back it all up. With a strong emphasis on cybersecurity, he develops robust global cloud strategies prioritizing data protection and resilience. Leveraging complexity theory, Shamir delivers innovative and elegant solutions to address complex requirements while driving business growth, positioning himself as a driving force in cloud transformation for organizations in the digital age.