
Confidential Computing: Attestation
Welcome back to our blog series on confidential computing! In our previous post, we provided an overview of confidential computing and the current state of the technology. Today, we’ll delve deeper into the concept of attestation, a crucial aspect of confidential computing that helps to prove the integrity and trustworthiness of computing environments. So, let’s jump right in!
What is attestation?
Before we can discuss attestation directly, we need to discuss the concept of trust and trustworthiness.
Trust refers to the belief or confidence that one party has in the reliability, competence, and honesty of another party. It is a subjective assessment based on past experiences, reputation, relationships, and other factors. Trust is often established over time through interactions and consistent behavior. The key point here is that trust is a choice that one system makes about another.
Trustworthiness in cybersecurity refers to the objective measure of the reliability, integrity, and security of a system, component, or entity. It assesses whether the entity can be relied upon to perform its intended functions securely and consistently. Trustworthiness is determined by factors such as the implementation of robust security controls, adherence to security standards and best practices, regular audits and assessments, and the ability to withstand attacks or breaches.
It follows then, that, attestation, in the context of confidential computing, refers to the process of verifying the integrity and authenticity of a computing environment. It enables parties to establish trust in the hardware, software, and configurations of a system, ensuring that it hasn’t been compromised or tampered with. The important part here is that attestation is simply the mechanism whereby one system asserts information about itself to another system. It is just one of the factors that a system can use to judge the trustworthiness of another system, and thereby, make a trust decision about that system.
Importantly, attestation in the context of confidential computing includes not only the process by which one system makes claims about itself, but also includes the processes by which those claims are verified to be true. This is one of the core components of the attestation component within the realm of confidential computing, as we will see below.
How does attestation work?
Here is the architectural overview from RFC9334:
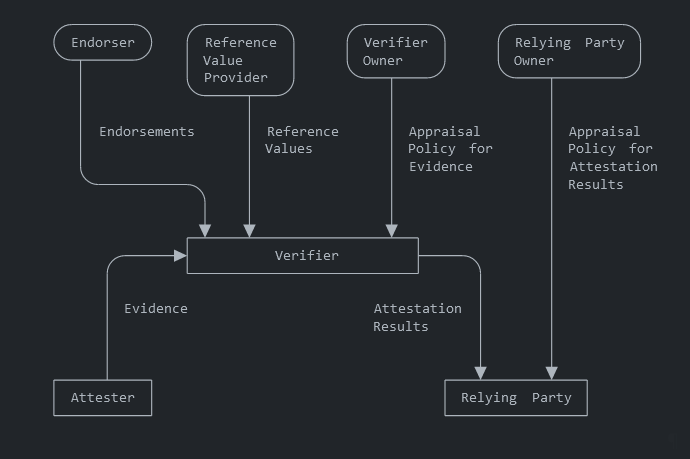
The relying party is attempting to make a trust decision about another system (the attester). One of the factors it considers when making this trust decision is the computing state of the attester. This includes evaluating claims about the hardware, software, and configuration of that system. The attester makes claims about itself in the form of providing evidence to a verifier. The verifier uses knowledge it has (endorsements, reference values) to appraise the evidence based on a configured appraisal policy. Once appraised, it provides the results of that appraisal to the relying party, which can then use those results in making a trust decision.
The process of evidence gathering needs to be strictly controlled. I will likely cover this in a future blog post but suffice it to say that there are certain patterns/practices that need to be followed so that evidence is collected appropriately to support the attestation process. This generally involves the concepts of an attesting environment (based on some sort of secure enclave technology) making assertions/claims about a target environment. Importantly, the attesting environment generally inspects the target environment for claims, rather than the target environment making claims about itself.
Another key point here is that the process of attestation does not define the rules that a verifier or relying party uses to make a trust decision. The attestation process is ultimately just an information gathering mechanism, where the claims have been attested in a way that the relying party can trust that the claims are true. The relying party still uses its custom appraisal policy, or other rules, to ultimately make access control decisions.
Conclusion
I’m hoping that the above discussion wasn’t too technical. Attestation is a critical concept in the realm of confidential computing, allowing for one system to make trustworthy claims about itself to another party. By verifying the authenticity of components and configurations, attestation helps establish trust between systems. As confidential computing continues to evolve, understanding and implementing robust attestation mechanisms will be crucial for safeguarding sensitive data and ensuring secure operations.
About Shamir Charania

Shamir Charania, a seasoned cloud expert, possesses in-depth expertise in Amazon Web Services (AWS) and Microsoft Azure, complemented by his six-year tenure as a Microsoft MVP in Azure. At Keep Secure, Shamir provides strategic cloud guidance, with senior architecture-level decision-making to having the technical chops to back it all up. With a strong emphasis on cybersecurity, he develops robust global cloud strategies prioritizing data protection and resilience. Leveraging complexity theory, Shamir delivers innovative and elegant solutions to address complex requirements while driving business growth, positioning himself as a driving force in cloud transformation for organizations in the digital age.