
AZ500 - Identity - Part 1
I am currently studying for the AZ500 exam which focuses on Microsoft Azure Security Technologies. This is the first blog post in that series.
The first major section in the AZ500 exam is focused on managing identity and access. The goal of this post is to provide a basic understanding of what is Azure active directory.
What is Azure Active Directory?
Azure Active Directory (Azure AD) is a cloud-based SaaS platform designed to help companies manage identities and access across numerous on-premises and cloud based services. Because Azure AD is designed as a service, you get many benefits simply by using the platform. This includes architectural components such as:
- Scalability
- Azure AD is globally distributed with a primary writable replica along with multiple secondary replicas that can handle read requests
- Continuous availability
- Azure AD makes use of a single-master service design which “includes a carefully orchestrated and deterministic primary replica failover process”
- Fault Tolerance
- Faults are auto-magically handled by the platform. In the event of primary/master failure, orchestration promotes a new primary. In the case of read replica failure, traffic is re-routed to other instances
- Data Durability
- Azure AD maintains a recovery time objective of 0. This is accomplished by having all writes synchronously commit to at least 2 data centers before being considered committed.
- Data consistency
- In general, Azure AD is eventually consistent. It does, however, provide read-write consistency within a session by immediately replicating writes to the read replica where the logical session’s reads were issued.
- Backup Protection
- Azure AD implements capabilities such as soft deletes and daily backups.
- Metrics and Monitors
- Microsoft actively monitors and manages the health of the Azure AD service and it’s underlying components for failures to try to achieve a time-to-detect of less than 5 minutes and a time-to-mitigate of less than 30 minutes
The following chart provides a good overview of all the different areas of Azure Active Directory.
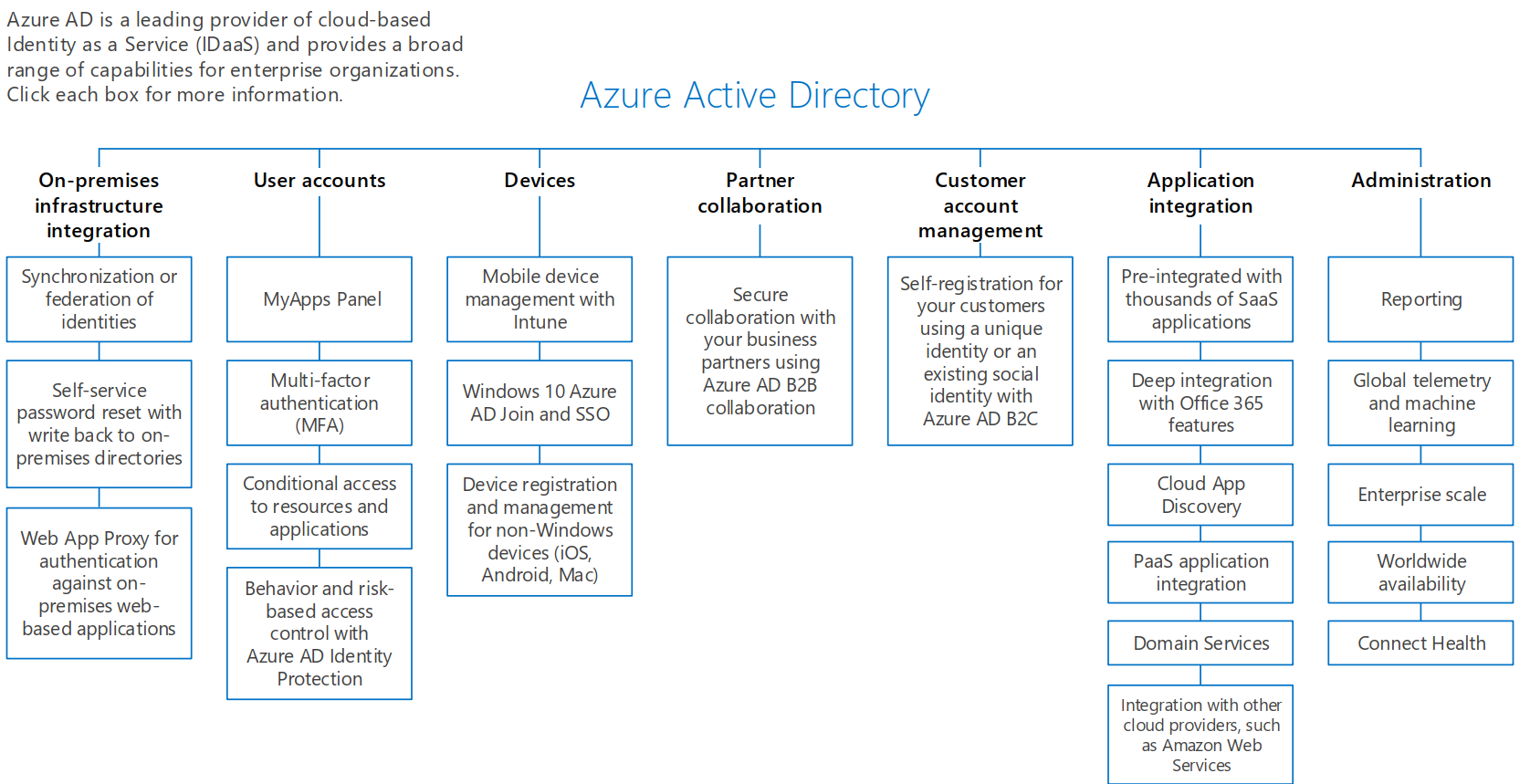
On the main page for Azure Active Directory documentation, it lists 3 uses (or, as I like to refer to them, intentions) for Azure AD. They list the 3 as IT Admins, App Developers, and Office/Azure/Dynamics Customers. Let’s start with the last one first.
Office/Azure/Dynamics Customers
Most organizations are using Azure AD because it comes as the authentication service that backs other Microsoft services such as office 365 and Azure. From an authentication standpoint, Azure effectively passes off the authentication process of a user to the Azure AD service, which authenticates the user, and then returns a set of claims/permissions that can then be consumed by Office 365/Azure/Dynamics in authorization decisions.
App Developers
Since Azure AD is a stand-alone identity service (IDaaS), it can be used to offline authentication considerations for custom built applications (and by extension, other SaaS applications). Azure AD is an Oauth 2.0 and OpenID Connect compliant authentication service.
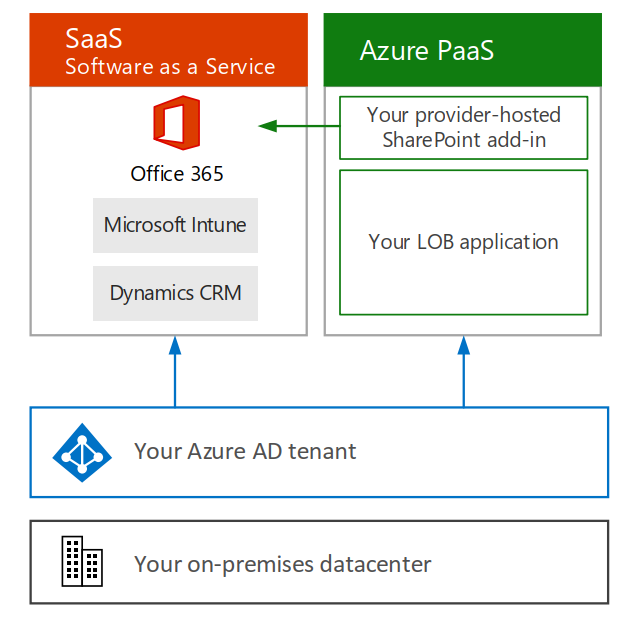
There are a couple of different “modes” that Azure AD can be configured in to allow for more complex authentication scenarios. For example, Azure business-to-business (B2B) can be used by organizations to provide “advanced trust relationships” so they can share data and services while separating the identity management concerns.
Lastly, Azure B2C (business-to-consumer) can be used to connect directly with customers either by allowing them to use their social logins or by managing a user store for you.
IT Admins
IT admins are going to mostly be interested in the management functionality of Azure AD as it relates to their organization. This includes features such as:
- Using “applications” to control access for automated processes and/or 3rd party applications
- Security features such as multi-factor authentication, advanced reporting, etc
- User integration scenarios backed by automation
- Integration with on-premises active directory
- Federation scenarios
Now that we have a basic understanding of what is Azure Active directory, we are ready to move on to talk about app registrations.
References
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-architecture
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-whatis
About Shamir Charania

Shamir Charania, a seasoned cloud expert, possesses in-depth expertise in Amazon Web Services (AWS) and Microsoft Azure, complemented by his six-year tenure as a Microsoft MVP in Azure. At Keep Secure, Shamir provides strategic cloud guidance, with senior architecture-level decision-making to having the technical chops to back it all up. With a strong emphasis on cybersecurity, he develops robust global cloud strategies prioritizing data protection and resilience. Leveraging complexity theory, Shamir delivers innovative and elegant solutions to address complex requirements while driving business growth, positioning himself as a driving force in cloud transformation for organizations in the digital age.