
Confidential Computing: OpenEnclave SDK
Welcome back to our blog series on confidential computing! In our previous post, we provided an overview of the concept of Attestation. Today, we’ll further our discussion by taking a look at an open source project that leverages technologies such as Intel SGX: the Open Enclave SDK.
Open Enclave SDK
Since the mid 2010’s, silicon manufacturers have been implementing trusted execution environments (TEEs) in their hardware architectures. The Open Enclave SDK(OE) is a project that aims to provide a hardware-agonostic, open source library for developing applications that utilize TEEs.
OE is an SDK for building enclave applications in C and C++. An enclave application consists of two components:
- An untrusted host application
- A trusted enclave application
In the diagram below from the OE documentation, we can see the components of a secure application and the flow of how a user’s request is processed.
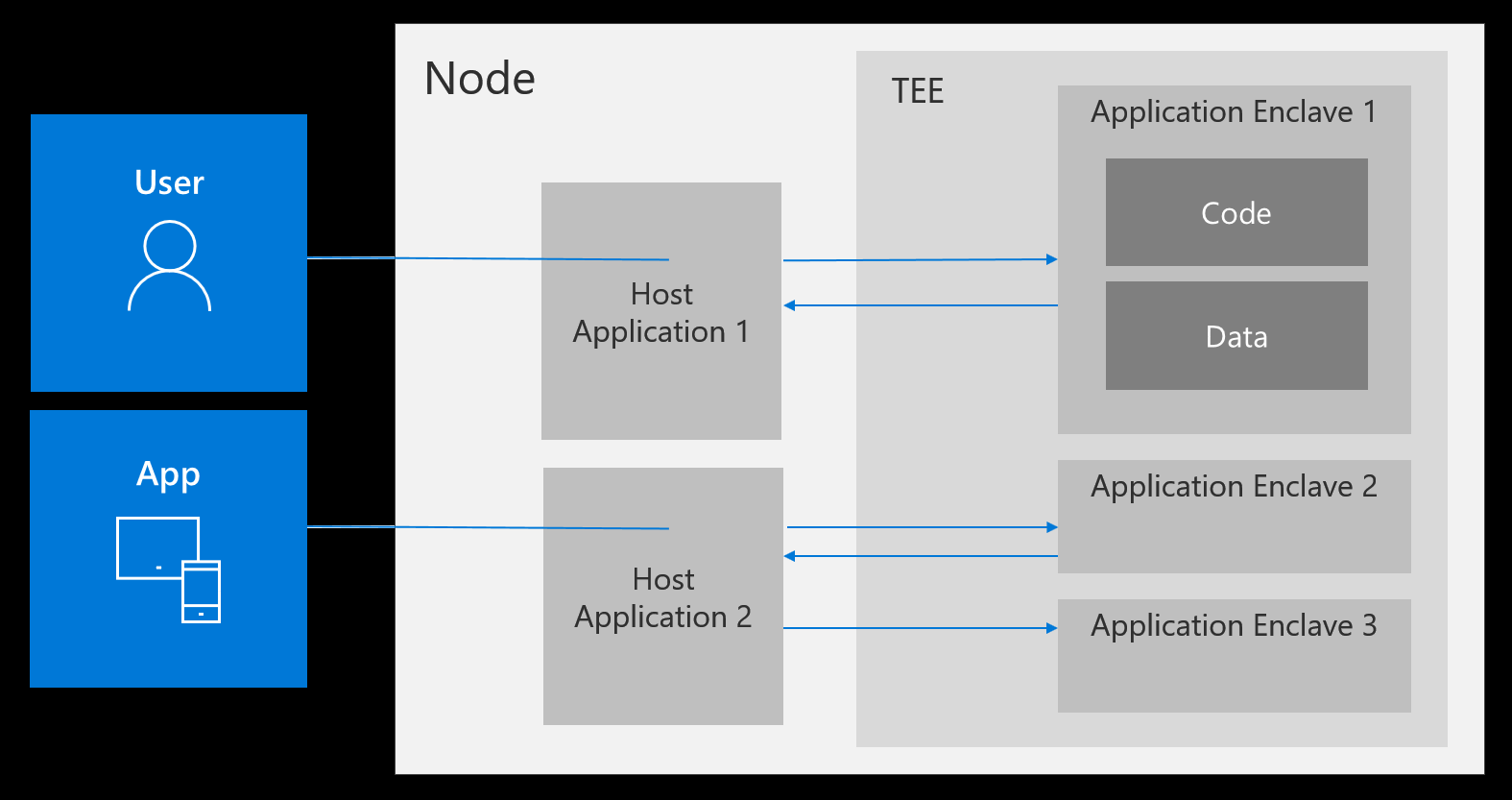 Image courtesy of https://openenclave.io/sdk/
Image courtesy of https://openenclave.io/sdk/
Host Application
The host application is the untrusted part of the application, running inside a conventional execution environment outside of the TEE. The host’s primary role is to manage and facilitate interations with the enclave, while handling tasks that dont need to be executed inside the enclave’s trusted environment.
Let’s take a closer look at some of the responsibilities of the host application.
Initialization of the Enclave
The host application is responsible for initializing the enclave and establishing a secure communication channel with it. This involves loading the enclave, setting up the neccessary data structures, and ensuring the enclave is properly configured.
Data Input and Output
The host handles data input and output for the enclave. When external data needs to be processed within the enclave, it’s the host that recieves the data and passes it to the enclave using ECalls(Enclave calls). On the flip side, when the enclave is finished processing the request and needs to return the data, the host handles the data exchange through Ocalls(Out calls).
Security boundary
As we saw with the data input/output process, the host serves as a security boundary between the TEE and the external world as the entry point to the enclave. It ensures that only authorized and validated requests are forwarded to the enclave for processing.
Enclave Lifecycle management
The host application can create and destroy enclaves as required. This is crucial for ensuring that enclaves are instatiated and terminated based on demand or specific use cases.
Enclave Application
The enclave application is the trusted part of the application running in a TEE. Enclaves are designed to provide a secure and isolated space where sensitive data can be processed, protected from unauthorized access and tampering.
Secure Execution
The primary role of the enclave is to execute sensitive and security-critical portions of an application. The enclave is running in a secure environment in a hardware-protected area of the CPU provided by the hardware vendor (such as Intel SGX). This means the enclave can only execute code that has been signed and verified.
Data Protection
Enclaves ensure the confidentiality and integrity of the data they process. Data within the enclave is encrypted and can only be accessed or modified by code running inside the enclave. This protection extends to both code and data, guarding against memory-based attacks.
Attestation and identity
Enclaves must be attested to prove their integrity to external parties. As we saw in our previous article on attestation, this is a critical peice of assuring trust between systems. The OE SDK provides a number of functions that can help to provide attestation reports and SGX quotes that can be verified to a relying party by another enclave or a cloud based verifying service, such as Microsoft Azure Attestation.
Secure Communication
Enclaves can only communicate with the host and other enclaves through secure channels using Ecalls and Ocalls. These calls ensure the data exchanged between the enclave and host, or enclave and enclave, is encrypted and authenticated.
Isolation
Enclaves provide strong isolation from the host and other enclaves. This isolation means that even if the host or another enclave is compromised, the contents of the enclave remain protected.
Conclusion
The Open Enclave SDK is a very promising open source technology that can be used to build secure applications. As hardware vendors continue to implement TEEs in their architectures, the OE SDK will be an important tool for building secure applications in C and C++.
About Tyler Fougere

Tyler is an AWS Certified Solutions Architect and has over a decade of enterprise systems administration experience, bringing a wealth of knowledge on Windows, Linux and MacOS infrastructure. You can find him most days and nights trying to quench an insatiable thirst for knowledge of all things cloud and technology.